Recently, Ledger (the makers of popular hardware wallets like the Nano S and Nano X) published an article in their blog where they explained how they validate the genuineness of their devices between the factory and the end user. The article is called ‘A Closer Look Into Ledger Security: the Root of Trust‘ and I invite you to read it before proceeding further into my post.
How Ledger Devices Prove They’re Genuine
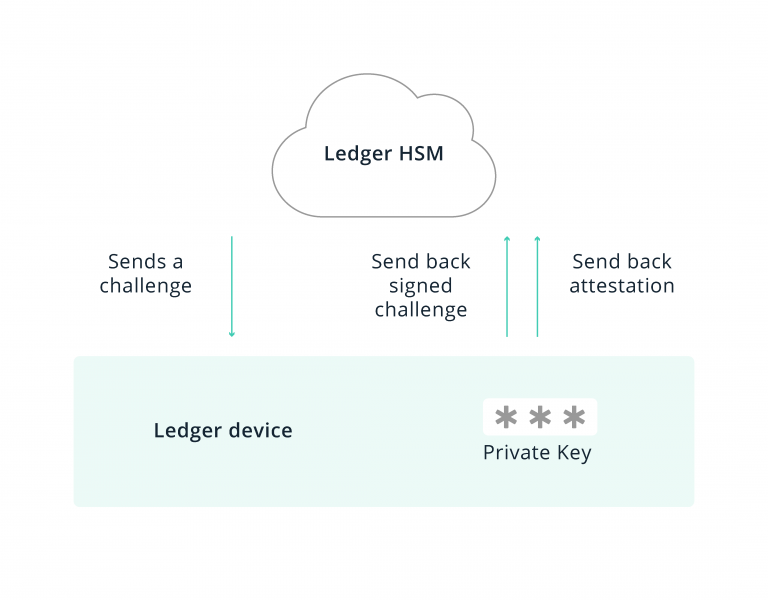
Ledger use an attestation mechanism which prevents a 3rd party producer from taking the same parts and manufacturing counterfeit Ledger devices that can then be used to steal customer funds. In essence, during manufacture each Ledger device creates its own private and public keys, and sends its public key to an authentication server called Ledger HSM. This server signs the public key with its own private key and sends it back to the device, where it is stored into read-only memory and can no longer be extracted. At later stages, the HSM server can challenge the Ledger device and ask it to sign an arbitrary message with its private key, as well as to send back its attestation (the pubkey signed with Ledger’s private key). In case these don’t match, the Ledger service will refuse to install firmware to the device, or add/remove/update applications installed on the device.
I claim that this solution, while viable for the purpose it has been built, may potentially create problems for users who use their Ledger devices to store multiple coins. The Ledger Nano S is particularly vulnerable, as it has very limited on-board memory and can store only a couple of coin apps at a time after a recent firmware update (see ‘Righting Out 1.5.5 Nano S Firmware Update‘, again on the Ledger blog).
Why This Is A Potential Problem
Ledger hardware devices use a common cryptographic core plus a number of ‘apps’ that provide support for different coins. The master seed is created in the device itself, and basic cryptographic primitives are handled there. Each app uses this master seed to create a master private key for the particular coin, and provides coin-specific crypto functions. Because the memory on the device is limited (this is not a fault of Ledger — secure ARM chips generally tend to have very little on-board memory), active crypto users are expected to add and remove crypto apps when they need to access different coins in their wallets.
And this is where things might get ugly. As explained in the first blog article:
1. The Ledger HSM stores copies of the public keys of all Ledger devices ever produced, and
2. All Ledger devices must prove they are genuine by signing a challenge with their private key and sending back the attestation of their public key whenever any of the following conditions are met (quote from the blog article below):
- When you are connecting your device to Ledger Live for the first time during the genuine check
- Each time you are accessing the Ledger Live manager (Or Ledger Manager chrome application)
- Every time you install an application from the Ledger Live manager (Or Ledger Manager Chrome application)
- Each time you are updating your firmware.
Do you see where this is going? Ledger have created a centralized point of failure that can render their devices almost if not completely inoperable, either because of unfortunate data loss, the intended actions of a malicious 3rd party, or government coercion. Ledger is a company based in France but also has offices in New York, San Francisco and Hong Kong, so presumably it can be fucked silly by all major governments (EU, USA, and China).
Of these three, only data loss can be prevented, as confirmed (vaguely) by the manufacturer:
Hello, thank you for reaching out.
We have a recovery process for our HSM if required. This would prevent loss of this data.
Regarding 3rd party wallets: installing applications onto your device requires connecting to the Ledger Live manager, where we verify genuineness.
— Ledger (@Ledger) February 25, 2019
However the possibility to DDoS their service or just shut it down by order of the police or courts remains a viable possibility. When that happens, users will lose the ability to add new apps to their Ledger devices and will no longer be able to move their coins away.
This might not be an issue for BTC owners, because the seed can be restored to any BIP39-compatible wallet (hardware, desktop, or mobile). But the more obscure the coins you are holding on your Ledger Nano S, the more likely you will lose access to them. As confirmed by Ledger’s own tech support & writer David da Silva Rosa, with XRP for example you will have no recourse:
Yeah there are some assets that have no BIP39 compatible wallet. XRP is one example. Recovery can only be done on a Ledger device for those.
— David da Silva Rosa ⚡️ (@dldasilvarosa) February 25, 2019
Many of the trashier alts have rudimentary software wallet support, and there have been many attempts at creating malicious wallets that steal coins; so for the majority of altcoin users, the Ledger Nano (or any other HW wallet, for that matter!) is the best chance at keeping funds safe.
It is worth mentioning that the Ledger Nano X has much more on-board storage and can hold up to 100 apps at the same time. Presumably, this would allow you to withdraw your funds more easily even if Ledger shuts down (although it remains unclear how exactly, given that the Ledger Live app relies on Ledger servers to send transactions…)
But the bottom line is that this approach of creating a single point of failure and locking multiple important functions with it makes the device inherently unreliable in the long run. You have been warned!

I am a small business owner from Bulgaria. I have been tinkering with personal computers ever since I was a kid. I feel enchanted by Bitcoin technology; last time I felt this excited was some 23 years ago when I first started surfing the internet using a 28.8k modem.
